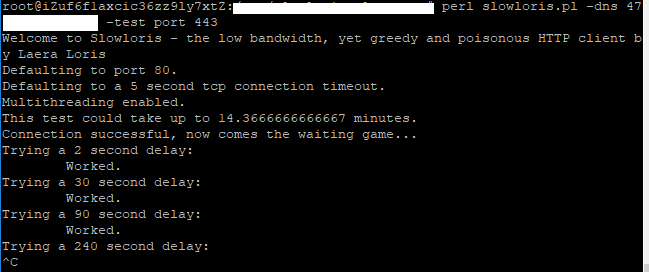
Description
The Apache server was found to be potentially vulnerable to the Slowloris denial of service attack. These attacks require small amounts of bandwidth and could be successfully carried out from only one computer. A Slowloris denial of service attacks attempt to overload the server by opening and maintaining multiple incomplete HTTP requests to the server at the same time. The following proof of concept shows that it was possible to keep connections opened for as long as 500 seconds, which is long enough to allow a successful DoS attack using Slowloris.
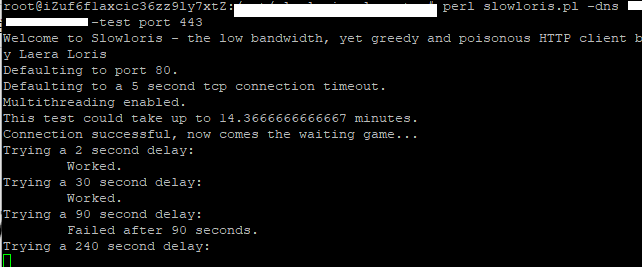
To avoid undesired impact, an attack was not attempted. This issue is therefore labelled as a potential denial of service.
Recommendation
Reconfigure the Apache server to limit the timeout of each connection:
<IfModule mod_reqtimeout.c>
RequestReadTimeout header=20,MinRate=500 body=20,MinRate=500
</IfModule>
The configuration above will terminate the connection if the client fails to send the header or body data within 20 seconds each. Please note that this timeout value should be design to limit the impact on legitimate users with slow connections, as their connections may be affected too.